Jenkins Pipeline Step: Outdated NPM Modules
How to keep on top of outdated dependencies as part of your CI and CD process, using npm-check-updates and Jenkins.
As I mentioned previously at HP, we make heavy use of Node.JS, and Jenkins for our build pipelines. We are also a security business, so any steps we can take to secure our code we take - previously I covered Checking for Vulnerable Modules, but now I'm going to simply do some checking for outdated modules in our package.json instead.
Prerequisites
This can all be achieved relatively easily in Jenkins by again making use of the Compiler Warnings plugin, so make sure you have this installed in Jenkins before we start.
You will also need to have the npm-check-updates module installed on your build server, easily done with npm install -g npm-check-updates.
Setting up the plugin
First things first, we need to configure the compiler warnings plugin. Basically all this plugin does is scan your build log and attempts to match on a given RegEx. To configure the plugin head over to your Jenkins Configuration page and scroll down to the Compiler Warnings section.
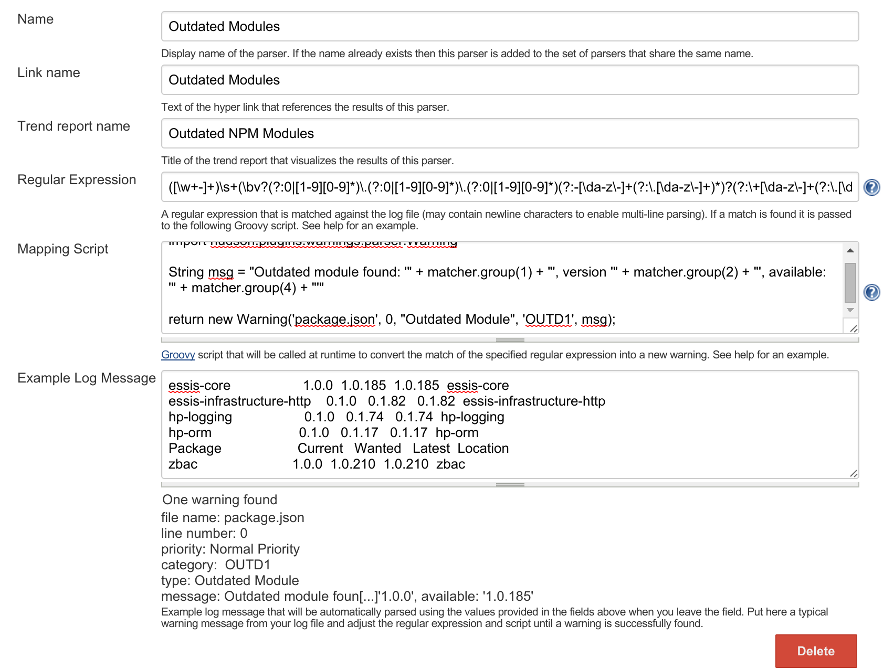
You want to create a new type of warning here with the following information:
- Name: Outdated Modules
- Link Name: Outdated Modules
- Trend Report Name: Outdated NPM Modules
The next bit you will need is the Regular Expression, brace your eyes here for a foul bit of regex! This is the result of much fine tuning to get to the point we don't have any false positives from other lines in the console.
([\w+-]+)\s+(\bv?(?:0|[1-9][0-9]*)\.(?:0|[1-9][0-9]*)\.(?:0|[1-9][0-9]*)(?:-[\da-z\-]+(?:\.[\da-z\-]+)*)?(?:\+[\da-z\-]+(?:\.[\da-z\-]+)*)?\b)\s+(\bv?(?:0|[1-9][0-9]*)\.(?:0|[1-9][0-9]*)\.(?:0|[1-9][0-9]*)(?:-[\da-z\-]+(?:\.[\da-z\-]+)*)?(?:\+[\da-z\-]+(?:\.[\da-z\-]+)*)?\b)\s+(\bv?(?:0|[1-9][0-9]*)\.(?:0|[1-9][0-9]*)\.(?:0|[1-9][0-9]*)(?:-[\da-z\-]+(?:\.[\da-z\-]+)*)?(?:\+[\da-z\-]+(?:\.[\da-z\-]+)*)?\b)\s+(.*)
And finally the mapping script is the part that takes the result from your RegEx and creates a hudson.plugins.warnings.parser.Warning object which Jenkins can recognise. Set it like this:
import hudson.plugins.warnings.parser.Warning
String msg = "Outdated module found: '" + matcher.group(1) + "', version '" + matcher.group(2) + "', available: '" + matcher.group(4) + "'"
return new Warning('package.json', 0, "Outdated Module", 'OUTD1', msg);
The priority here, as it is omitted from the instantiation of the Warning defaults to normal.
Example Log Message, to save you some time, here is an example output from the module:
Package Current Wanted Latest Location
essis-core 1.0.0 1.0.185 1.0.185 essis-core
essis-infrastructure-http 0.1.0 0.1.82 0.1.82 essis-infrastructure-http
hp-logging 0.1.0 0.1.74 0.1.74 hp-logging
hp-orm 0.1.0 0.1.17 0.1.17 hp-orm
zbac 1.0.0 1.0.210 1.0.210 zbac
With all those bits in, your page should look like this:
Adding a Build Step
You will need to add a build step now that executes the npm-check-updates package we installed earlier. This is quite simple, go into jenkins and add a new Shell build step, and in it just add nsp-check-updates --depth=0.
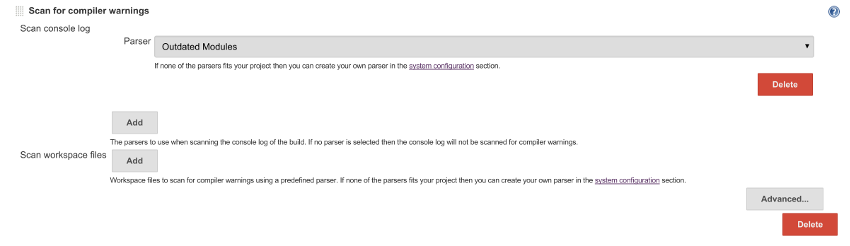
Post-Build Action
The next step is to add a post build action to the project, the screenshot below shows a configuration that will report on the number of outdated modules found.
The important settings here are:
- Parser: Outdated Modules
- And the tick box in Compute New Warnings
That's it
At this point if you run your job (and there are any detected out of date modules) you will see this in your build log:
09:24:30 => npm outdated --depth=0
09:24:38 Package Current Wanted Latest Location
09:24:38 async 1.3.0 1.3.0 1.4.0 async
09:24:38 hapi 6.7.1 6.7.1 8.8.0 hapi
09:24:38 joi 6.5.0 6.5.0 6.6.1 joi
And your build will go red.
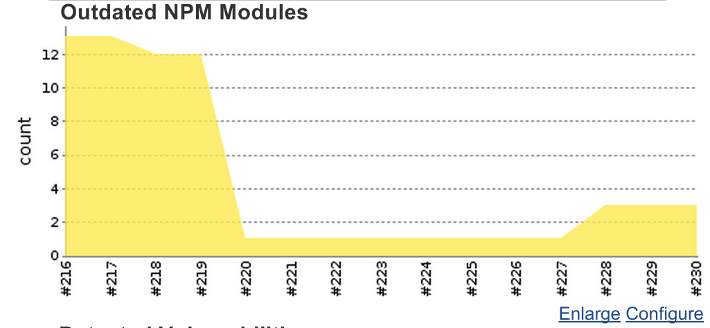
You will also get a nice little graph of your outdated modules over time:
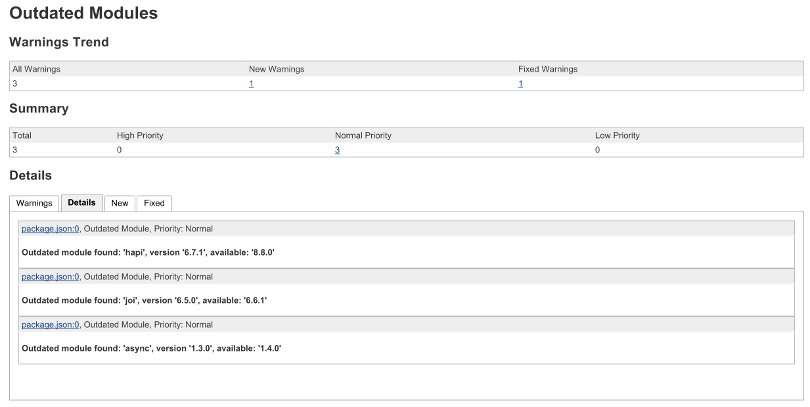
And also, on the build page, you can view the report:
I hope this article was of use, any questions just ask.
